The numbers behind a cyber pandemic – detailed dive
*Updated 14.12.2021 06:00 PST
Precisely one year after the SolarWinds Hack, the groundbreaking supply chain attack the world experienced, and while organizations are still struggling to protect the software supply chain from third-party risk, the Apache Log4j vulnerability exploit has caught security teams during a weekend. Unlike other major cyber-attacks that involve one or a limited number of software, Log4j is basically embedded in every Java based product or web service. It is very difficult to manually remediate it. Once an exploration was published (on Friday), scans of the internet ensued (to allocate surfaces which are vulnerable due to this incident). Those who won’t implement a protection are probably already scanned by malicious actors.
Since Friday, December 9th, when the vulnerability was reported, actors around the world are on the lookout for exploits. The number of combinations of how to exploit it give the attacker many alternatives to bypass newly introduced protections. It means that one layer of protection is not enough, and only multi-layered security posture would provide a resilient protection. Three days after the outbreak, we are summing up what we see until now, which is clearly a cyber pandemic that hasn’t seen its peak yet.
A true cyber – pandemic
Diving into the numbers behind the attack, gathered and analyzed by Check Point Research, we see a pandemic-like spread since the outbreak on Friday, by the beginning of the week, on Monday.
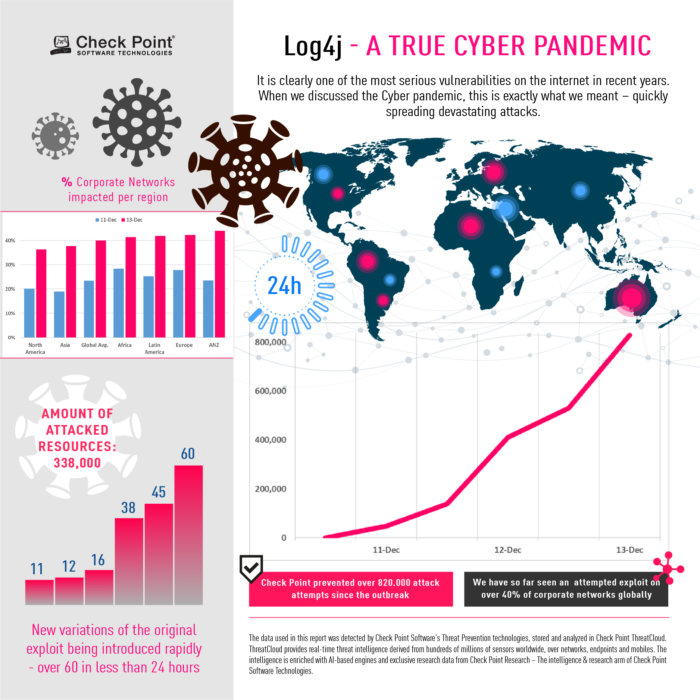
Early reports on December 10th showed merely thousands of attack attempts, rising to over 40,000 during Saturday, December 11th. Twenty-four hours after the initial outbreak our sensors recorded almost 200,000 attempts of attack across the globe, leveraging this vulnerability. As of the time these lines are written, 72 hours post initial outbreak, the number hit over 800,000 attacks.
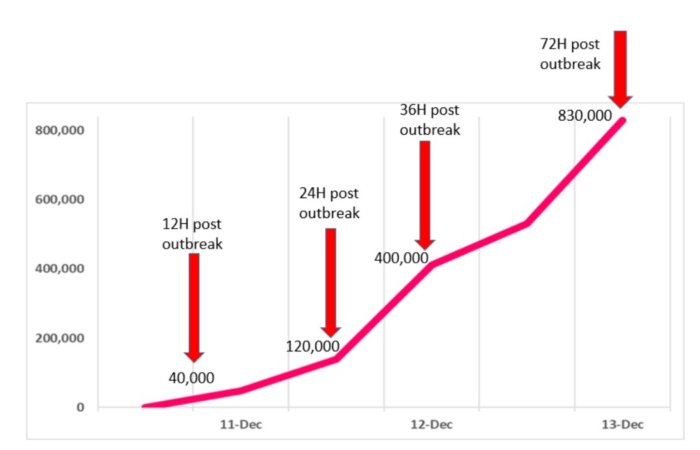
It is clearly one of the most serious vulnerabilities on the internet in recent years, and the potential for damage is incalculable.
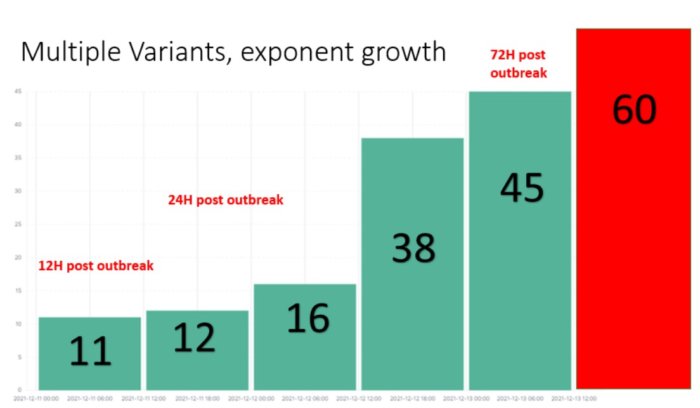
Check Point Research witnessed new variations of the original exploit being introduced rapidly- over 60 in less than 24 hours.
When we discussed the Cyber pandemic, this is exactly what we meant – quickly spreading devastating attacks.
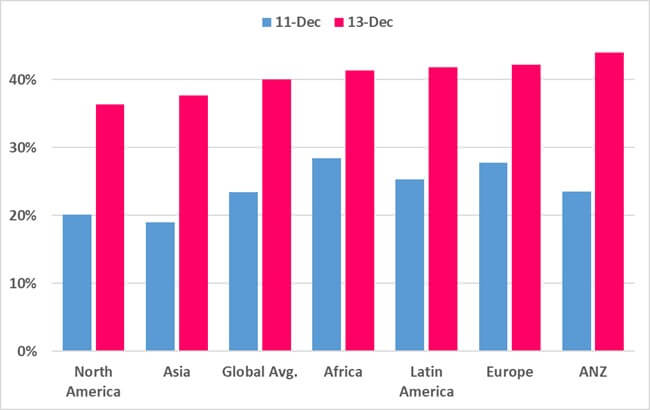
Corporate networks impacted globally
One of the most dramatic characteristics of a cyber pandemic are major vulnerabilities in popular software and services, which impact an enormous number of organizations across the globe, spreading like wild fire.
Since we started to implement our protection we prevented over 1,272,000 attempts to allocate the vulnerability, over 46% of those attempts were made by known malicious groups.
We have so far seen an attempted exploit on almost 44% of corporate networks globally
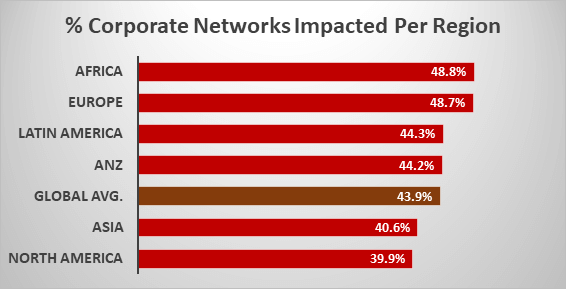
Corporate numbers impacted by countries
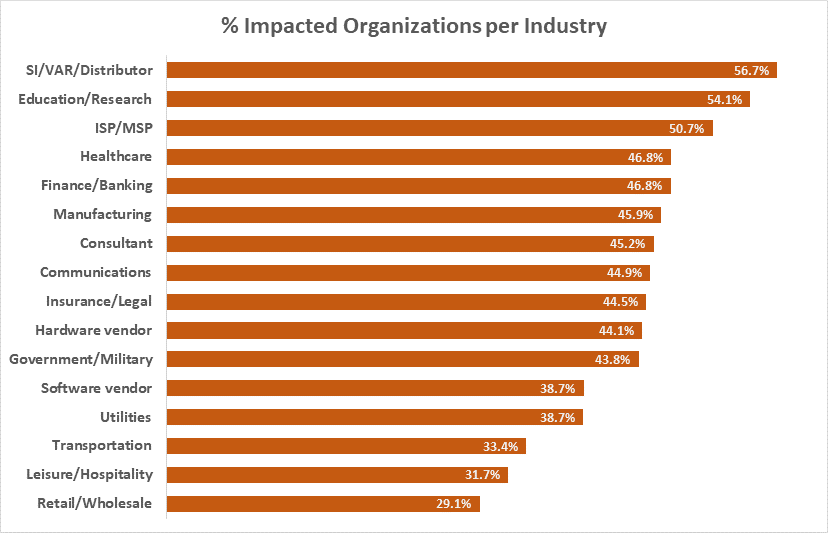
The spread per countries is overwhelming and crosses continent and regions, ranging to over 90 countries in all regions. The impact itself is also wide and reaches peaks of countries seeing over 60% of corporate networks impacted, and many distributions seeing over 50% of corporate networks within the country beings impacted.
*A detailed breakdown per countries included in Annex 1
The Brain behind Check Point’s threat prevention
The statistics and data used in this report present data detected by Check Point’s Threat Prevention technologies, stored and analyzed in ThreatCloud. ThreatCloud provides real-time threat intelligence derived from hundreds of millions of sensors worldwide, over networks, endpoints and mobiles. ThreatCloud is actually the brain behind Check Point Software’s threat prevention power, combines big data threat intelligence with advanced AI technologies to provide accurate prevention to all Check Point Software customers.
Instant protections from the most significant unknown software vulnerabilities
All software vulnerabilities that are found by CPR or seen in the wild, such as Log4j, are immediately fed to ThreatCloud, which propagates the appropriate protections throughout Check Point’s products, so that all Check Point customers are instantly protected with no patching needed. That is exactly what happened last weekend. As soon as the Log4j vulnerability was reported on December 9, all relevant protections were propagated through all of Check Point products (refer to sk176884).
Conclusion
This vulnerability, because of the complexity in patching it and easiness to exploit, seems that it will stay with us for years to come, unless companies and services take immediate action to prevent the attacks on their products by implementing a protection.
Since the outbreak of the COVID-19 pandemic, society has already gotten used to learning about variants, spread and other terminology that is taken from epidemiology theories. The phenomena the world is witnessing with the exploitation of this vulnerability is very much identical.
Given the upcoming holiday seasons, when security teams may be slower to implement protective measure, the threat is imminent. This acts precisely like a cyber pandemic — highly contagious, spreads rapidly and has multiple variants, which force more ways to attack.
How can Check Point Help?
Check Point Infinity provides protection against the Log4j Vulnerability.
We invite you to visit our dedicated website to learn more about this vulnerability and how Check Point products ensure you stay protected
To help customers, we are providing informative and actionable resources based on our R&D teams’ experience, expertise and insights.
We will continue to update on any new development of this significant security event.
Our technical support teams are available for you 24/7 and we are all at your service to make sure you’ll stay protected.
Annex 1 – Detailed breakdown – Impact per country
| Top values of country name | Impact |
| Angola | 41% |
| Argentina | 46% |
| Australia | 49% |
| Austria | 56% |
| Bahrain | 30% |
| Belarus | 37% |
| Belgium | 52% |
| Bolivia | 39% |
| Bosnia and Herzegovina | 59% |
| Brazil | 53% |
| Bulgaria | 44% |
| Canada | 47% |
| Chile | 46% |
| China | 32% |
| Colombia | 50% |
| Costa Rica | 45% |
| Croatia | 42% |
| Cyprus | 46% |
| Czechia | 55% |
| Denmark | 58% |
| Dominican Republic | 36% |
| Ecuador | 38% |
| El Salvador | 26% |
| Estonia | 54% |
| Finland | 42% |
| France | 47% |
| Georgia | 32% |
| Germany | 51% |
| Greece | 58% |
| Guatemala | 34% |
| Honduras | 52% |
| Hong Kong | 46% |
| Hungary | 52% |
| India | 43% |
| Indonesia | 43% |
| Ireland | 54% |
| Israel | 54% |
| Italy | 50% |
| Jamaica | 45% |
| Japan | 37% |
| Kazakhstan | 38% |
| Kenya | 50% |
| Kuwait | 33% |
| Latvia | 41% |
| Luxembourg | 48% |
| Macao | 46% |
| Macedonia | 45% |
| Malaysia | 47% |
| Malta | 49% |
| Mexico | 32% |
| Mongolia | 62% |
| Morocco | 42% |
| Nepal | 64% |
| Netherlands | 46% |
| New Zealand | 48% |
| Nicaragua | 43% |
| Nigeria | 32% |
| Norway | 56% |
| Panama | 40% |
| Paraguay | 54% |
| Peru | 46% |
| Philippines | 49% |
| Poland | 49% |
| Portugal | 47% |
| Qatar | 41% |
| Republic of Korea | 40% |
| Republic of Lithuania | 24% |
| Romania | 32% |
| Russia | 48% |
| Saudi Arabia | 27% |
| Serbia | 56% |
| Singapore | 41% |
| Slovakia | 47% |
| Slovenia | 61% |
| South Africa | 51% |
| Spain | 43% |
| Sri Lanka | 11% |
| Sweden | 55% |
| Switzerland | 44% |
| Taiwan | 42% |
| Thailand | 38% |
| Trinidad and Tobago | 58% |
| Turkey | 57% |
| Ukraine | 39% |
| United Arab Emirates | 40% |
| United Kingdom | 42% |
| United States | 40% |
| Uruguay | 44% |
| Uzbekistan | 19% |
| Vietnam | 30% |
| Zambia | 48% |
Tuesday, December 14, 2021

